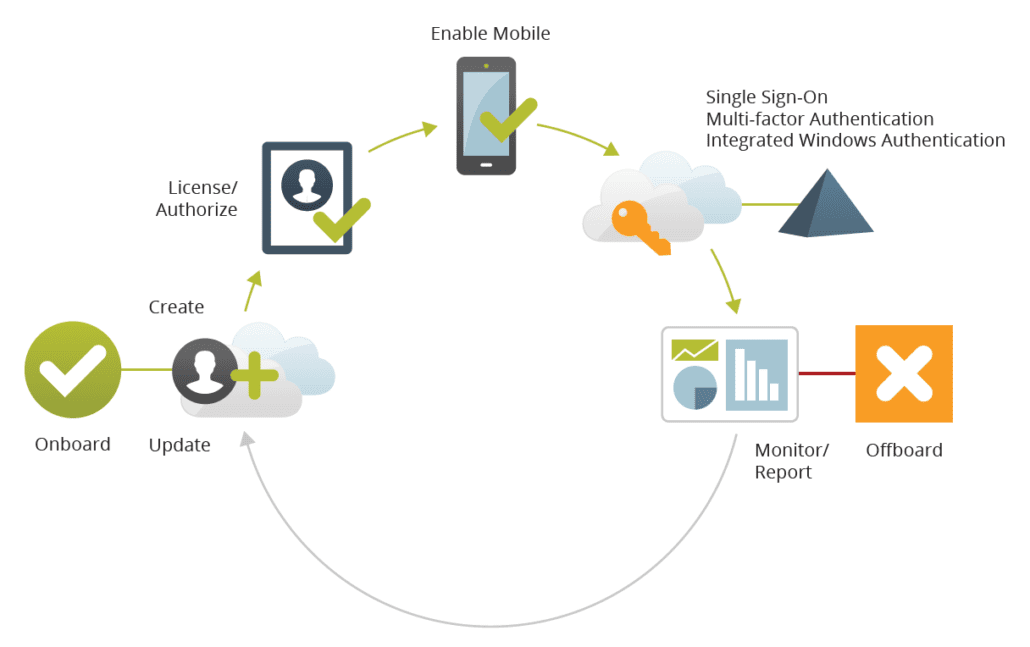
Top Six Things to Consider with an Identity-as-a-Service (IDaaS) Solution – Blog 4 of 6
4. Mobile Access Management
 Mobile has become the de facto way to access cloud apps requiring you to ensure security and enable functionality of users devices. This includes deploying appropriate client apps to the right device and ensuring an appropriately streamlined mobile experience. Unfortunately, most existing Identity and Access Management as a Service (IDaaS) solutions fall short when
Mobile has become the de facto way to access cloud apps requiring you to ensure security and enable functionality of users devices. This includes deploying appropriate client apps to the right device and ensuring an appropriately streamlined mobile experience. Unfortunately, most existing Identity and Access Management as a Service (IDaaS) solutions fall short when
it comes to mobile support because they were built and architected before it became clear that mobile devices (smart phones and tablets) were going to become the preeminent means to access apps. Instead, they are very web browser centric—i.e. their mobile IDaaS experience just supports web-based apps vs. also supporting rich mobile apps and device security. They also
provide no means to ensure that the user’s mobile device is trusted and secure, and while they may provision a user in the cloud service, they ignore giving the end user the corresponding app on their device.
Consequently, you should look for an IDaaS solution that allows your users to enroll their mobile devices and deliver strong authentication mechanisms (using PKI certificates). The solution should let you apply mobile device-specific group policies to ensure the underlying device is secure (e.g., ensure that a PIN is required to unlock the phone, etc.), detect jailbroken or rooted devices, and allow you to remotely lock, unenroll or wipe a lost or stolen device. Once you associate the device with a user and can trust the device you can leverage the device as an identifying factor for the user in cases where additional factors are required for multifactor and step-up athentication.
The solution should also provide unified app management for both web-based and mobile client apps. This ensures that users are not left with partial access or access defined and managed in separate silos of access management such as separate mobile device management solutions (MDM). Both app and mobile management should share the same roles, identities, management tools, reports and event logs. This unification of mobile and app access management reduces redundant tools, processes and skillsets.
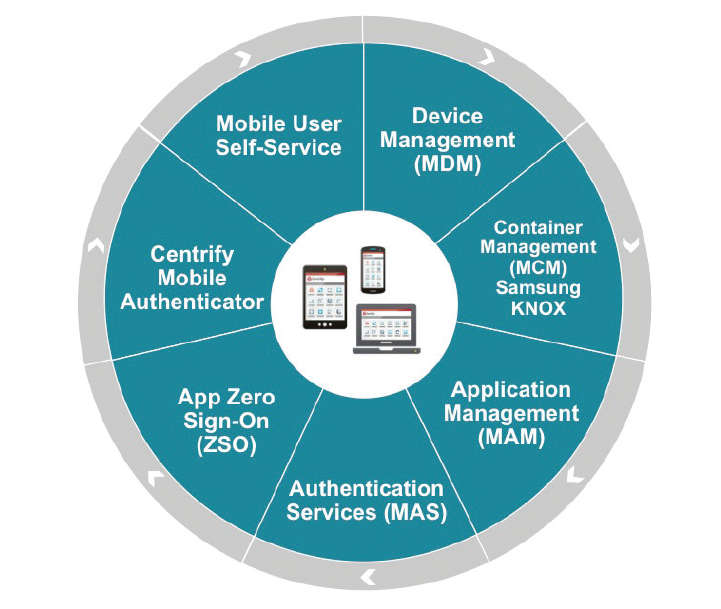

Mobile has quickly become the de facto way to
access apps. Centrify uniquely unifies app and
mobile access management.