IBM – Keeping Sensitive Data Secure In The Age Of Cloud Computing
/in IBM/by Howard Mahoney
Overcoming the challenges of protecting data that is here, there and everywhere. As cloud computing becomes pervasive, security fundamentals remain the same – secure and protect data and support compliance. The white paper discusses today’s security challenges in four key areas:
- Deploying in a cloud environment
- Cloud security challenges
- Organizational challenges
- Data protection approach
Cloud Identity for Dummies eBook
/in Cloud, Cloud IAM, IBM/by Howard Mahoney Secure access into applications and identity management is a complex and important topic. Many organizations struggle to keep up with IAM and seek a better solution. Deploying IAM as a cloud-based IDaaS solution solves the challenges of organizations facing increasing complexity, costs, and security compliance requirements. IDaaS lowers TCO, simplifies architecture, improves security and compliance, and provides seamless SSO integration for on-premises, SaaS, and mobile applications. The focus of this book is learning what IDaaS provides, why it benefits organizations, and how to implement it for your applications. A great deal of attention is given to explain IAM and cloud computing so you understand the context and benefits of a cloud-based IAM solution, which is IDaaS. Download IBM Cloud Identity for Dummies eBook
Secure access into applications and identity management is a complex and important topic. Many organizations struggle to keep up with IAM and seek a better solution. Deploying IAM as a cloud-based IDaaS solution solves the challenges of organizations facing increasing complexity, costs, and security compliance requirements. IDaaS lowers TCO, simplifies architecture, improves security and compliance, and provides seamless SSO integration for on-premises, SaaS, and mobile applications. The focus of this book is learning what IDaaS provides, why it benefits organizations, and how to implement it for your applications. A great deal of attention is given to explain IAM and cloud computing so you understand the context and benefits of a cloud-based IAM solution, which is IDaaS. Download IBM Cloud Identity for Dummies eBook
WebSphere SAML SP for ISIM SSO
/in IBM, ISIM, SAML, SSO, Uncategorized, WebSpher Application Server/by Howard MahoneyUse Case
Provide Federated single sign-on (SSO) capabilities for IBM Security Identity Manager without the use of IBM Security Access Manager. IBM’s documentation for ISIM explicitly defines how to configure SSO with the use of ISAM’s WebSEAL Authentication. After further investigation and prototyping, SSO capabilities using a third party IdP (Okta) have been successfully implemented into a live environment.
How to Configure
To configure single sign-on with the WebSphere SAML SP, Trust Association Interceptor and third part IdP, complete the following steps:
1. Deploy WebSphere SAML SP
WebSphere supports SAML web SSO and serves as the service provider for ISIM. WebSphere will consume the SAML Assertion from our IdP and establish a security context for the user into ISIM.
2. Configure WebSphere Trust Association Interceptor
Enable Trust Association for the Assertion Consumer Service deployed with WebSphere. The TAI will validate the request from a third-party IdP and will then perform an identity lookup to verify the user exists in ISIM.
3. Configure ISIM for SSO
To reiterate, the Knowledge Center documentation for ISIM states you are required to use IBM Security Access Manager to accomplish SSO, but this is not the case. There are a few properties that must be configured to prepare ISIM for SSO. Once these properties are enabled, the ISIM console and ISIM self-service login pages will be expecting SSO as the method of authentication.
4. Configure ISIM Security Domain
The deployment of the ISIM application creates its own security domain, named ISIMSecurityDomain. For ISIM to invoke the TAI there are three TAI properties which must be set within the ISIM security domain. These properties tell the security domain to leverage the TAI which contains the triggers, login URLs, and other ID mapping properties to complete SSO.
**NOTE** Application security is enabled by default for ISIM. For any application using TAI, application security must be enabled.
5. Enable Trust Association Interceptor
Once the Assertion Consumer Service, Trust Association Interceptor, and various properties are configured the next step is to enable the TAI for Global Security.
Assumptions
There are a few key assumptions to completing the configuration of the WebSphere SAML SP and SSO.
- Knowledge of deploying WebSphere middleware applications
- Certificate management
- Preconfigured and functioning IdP
- Understanding of Security Context for WebSphere applications
- General understanding of SAML

Joshua Moore
PathMaker Group Consultant
PathMaker Group Helps Protect the Power Grid With Policy-Based Identity & Access Management
/0 Comments/in Access Management, IBM, Identity Management/by PathMaker GroupPathMaker Group helped Westar Energy implement Identity & Access Management solutions from IBM that help their organization to easily administer, manage and monitor user access across its complex environment.
Hear directly from PathMaker Group Vice President, Chris Fields, alongside of Westar IT Security Systems Manager, Dave Adams, on a brief overview of the need, solution, and benefit.
Directory Object Search
/0 Comments/in DirectoryObjectSearch, IBM, IBM Tivoli Identity Manager, Identity Management, LDAP Search, Provisioning, Tivoli Identity Manager/by Mark AdamsonHave you ever wanted to perform an LDAP search in a workflow to check for … well let’s just say a duplicate UNIX UID.
In this example the account add workflow is checking to make sure the Unix UID is not in use by another account. The requirements in this instance are that UNIX UID can only be used once in a service. Once the duplicate is found the next step is up to you but in this case the account add was rejected.
First thing you have to do is expose the dataservices model. Add the following line to scriptframework.properties.
ITIM.java.access.dataservices=com.ibm.itim.dataservices.model.*
Example Script in Workflow Script Node:
This script node is from an Account Add workflow. The script gets the service DN and erposixuid from the new account. The service DN and UNIX UID are used to verify the UNIX UID has not been used before in the same service. The Directory Object Search will search ITIM’s LDAP as you can see from the search base. There are also a couple examples to get the account attributes.
/* Search the current service for an account with the same unix uid */
var myAccount = account.get();
var myPerson = owner.get();
var unixUidMatch = ‘false’;
var dupAccountList = ”;
errorInd.set(‘false’);
/* Get Service DN */
var myServiceDN = myAccount.getProperty(“erservice”)[0];
var myInputPosixUid = myAccount.getProperty(“erposixuid”);
if (myInputPosixUid != null && myInputPosixUid.length > 0)
myInputPosixUid = myInputPosixUid[0];
else
myInputPosixUid = “unknown”;
if (myInputPosixUid != “unknown”) {
/* Search Accounts within Service for unix UID */
var searchFilter = ‘(&(erservice=’ + myServiceDN + ‘)(erposixuid=’ + myInputPosixUid + ‘))’;
var searchBase = ‘ou=accounts,erglobalid=00000000000000000000,ou=XXX,O=XXX’;
var base = new com.ibm.itim.dataservices.model.DistinguishedName(searchBase);
var params = new com.ibm.itim.dataservices.model.SearchParameters();
var search = new com.ibm.itim.dataservices.model.DirectoryObjectSearch();
var results = search.fetch(base, searchFilter, params).iterator();
while (results.hasNext()) {
/* Duplicate Unix UID Found */
var dirObj = results.next().getDirectoryObject();
/* Get Account Object */
var mySearchAccount = new Account(dirObj.getDistinguishedName().toString());
var mySearchEruid = mySearchAccount.getProperty(‘eruid’);
if (mySearchEruid != null && mySearchEruid.length > 0) {
mySearchEruid = mySearchEruid[0];
if (unixUidMatch == ‘true’)
dupAccountList = dupAccountList + ‘ ,’+ mySearchEruid;
else
dupAccountList = mySearchEruid;
}
unixUidMatch = ‘true’;
}
OR
while (results.hasNext()) {
var dirObj = results.next().getDirectoryObject();
var myDupAccountID = dirObj.getAttribute(“eruid”);
if (myDupAccountID!=null) {
myDupAccountID = myDupAccountID.getValueString();
}
}
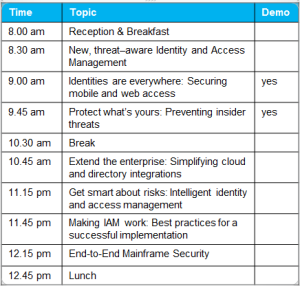
20/20 Vision: Identity and Access For The Next Decade
/0 Comments/in Access Management, Events, IBM, Identity Management/by PathMaker GroupAs attacks become more difficult to detect and defend, and threats
continue to grow, no organization is immune from security breaches.
We anticipate a shift around identity and access management (IAM) as
enterprises cope with increased regulatory compliance requirements,
insider and external threats, cloud integration, and more.
IBM Security threat aware IAM solutions help prepare you for current and
future security challenges with identity intelligence and secure online
access in mobile, cloud, mainframe, and social environments.
Explore IBM Security identity and access management
Join IBM and Pathmaker Group and learn how to:
• Use security intelligence to improve user oversight and compliance.
• Respond effectively to the rising number of identity focused attacks.
• Safeguard access within mobile, cloud, mainframe and social
environments.
• Protect against advanced insider threats.
Don’t miss this chance to network with your peers, talk to IBM security
experts, and get practical advice for your own IAM environment.
A Sobering Day for All CEOs
/0 Comments/in Access Management, IBM, IBM QRadar, Identity Management, Incident Response, PathMaker Group, Penetration Testing, Planning, Security Access Manager, Security Awareness, Security Services, Threat Management, Vulnerability Management/by Keith SquiresSadly, the CEO presiding over Target during the recent data breach resigned today. See USA today article.
This series of unfortunate events for Target begs a key question relating to the risks every company CEO faces today. Did Target leadership ask the right questions about overall IT security and the risk every company faces?
Protecting a company from Cyber bad guys is a never ending battle. It’s a game of leap frog with some serious consequences if you get behind. With all the opportunity for full-time, professionally paid, government backed hackers to spend all day every day figuring out new ways to wreck a company, the priority for combating this enemy needs to be pretty high on the list for every CIO and CEO. But it’s not just about spending all the money you can afford to spend. It’s about understanding where to spend the money on the right technology.
How do leaders responsible for protecting a company sort out all the noise from the real threats? This has become a constant exercise in analyzing risk and applying financial priorities accordingly.
As fast as the bad guys are coming up with new ways to exploit a target, new innovative minds are working to counter their moves. Many of these great technologies are being folded into a portfolio of products and solutions that can be layered across an enterprise to protect and prevent the latest threats from creating the worst kind of headlines.
IBM has been on a major buying spree for the last several years snapping up some of the best and brightest technologies and resources across the globe. They are quickly assembling an array of tools that are being shaped into the worlds best security risk analysis platform. By leveraging this risk-based assessment direction, IT leaders can depend on technologies that will not only provide the intelligence about where to address risk, but can be assured that these technologies are probably the best that money can buy.
IBM is currently the third largest security company in the world with the goal of being the largest and the best. As a Premier IBM Business Partner, we see this investment first hand. See ComputerWorld’s perspective.
PathMaker Group serves our customers by planning, implementing, and managing these security solutions across the enterprise. IT Security is a rapidly changing, complex business and our partnership with IBM helps us keep our customers one step ahead of the bad guys.
Have you had your Security Wellness Check?…
/0 Comments/in IBM, PathMaker Group, Penetration Testing, Policy Development, Security Assessments, Security Awareness, Security Framework, Security Services, Strategic Planning, Threat Advisories, Threat Management, Vulnerability Management/by PathMaker GroupSo you think your organization is secure . . . think again! IBM X-Force 2013 mid-year report says that many of the breaches recently reported were a result of “poorly applied security fundamentals and policies and could have been mitigated by putting some basic security hygiene into practice.” Covering the basics is exactly what we help companies achieve through our “SecurePath” 16 domain rapid security assessment. In one week we can review your security posture, cover all your bases and help you prioritize the big security gaps in your environment.
Identity and Access Management Best Practices Webinar
/0 Comments/in Access Management, IBM, Identity Management/by Chris FieldsHow Levi leveraged Identity Management infrastructure to enable “just in time” fully automated privileged system access
Presented by:
- Chuck Lankford, Global Director of Security at Levi Strauss & Co.
- Chris Fields, Vice President of Security Strategy, PathMaker Group
- Ravi Srinivasan, Director of IBM Security, Strategy, and Product Management
In our 50 minute webinar you will:
- Learn about the latest market trends in Identity and Access Management
- See why the IBM IAM Suite is one of the hottest sellers in the last six months
- See what’s new with the IBM IAM Suite including upcoming features and capabilities
- Hear what customers are buying and why
- Learn the five most common benefits from a robust IAM infrastructure
- Learn about best practices for implementing provisioning, access management, federation
- Hear customer use cases and their key business drivers for IAM

About the key presenter, Chuck Lankford:

About Chris Fields:
 About Ravi Srinivasan:
About Ravi Srinivasan:
Who We Are
PathMaker Group is a specialized Security and Identity Management Consultancy, blending core technical and product expertise, consultative know-how, and extensive implementation experience.
Pathmaker Group
DALLAS-FORT WORTH
635 Fritz Drive
Suite 110
Coppell, TX 75019
(817) 704-3644
info@pathmaker-group.com


